Map and Expose Your AI Attack Surface
.png)
See the Unseen
RedGraph applies graph theory to expose unintended connections across your agentic systems. Use RedGraph to instantly map every agent and its building blocks, including tools, MCP servers, data access, permissions and business use cases.
- Zero-Code Integration: Connect via URL or user authentication
- Graph-Based Visibility: Reveal hidden connections across your agentic systems
- Context-Aware Mapping: Spot logic flaws in real-world integrations

Validate With Real Exploits
RedGraph deploys autonomous adversarial agents that think like attackers - probing your deployed agents, pivoting when blocked, and proving exactly how vulnerabilities can be exploited. This approach also uncovers 'toxic combinations' by tracing how safe tools are chained together to create risks.
- Dynamic Multi-Turn Testing: Probe logic and defenses systematically
- Exploitable Risk Focus: Validate real threats, ignore theoretical noise
- Autonomous Adversaries: Mimic hacker pivoting at scale
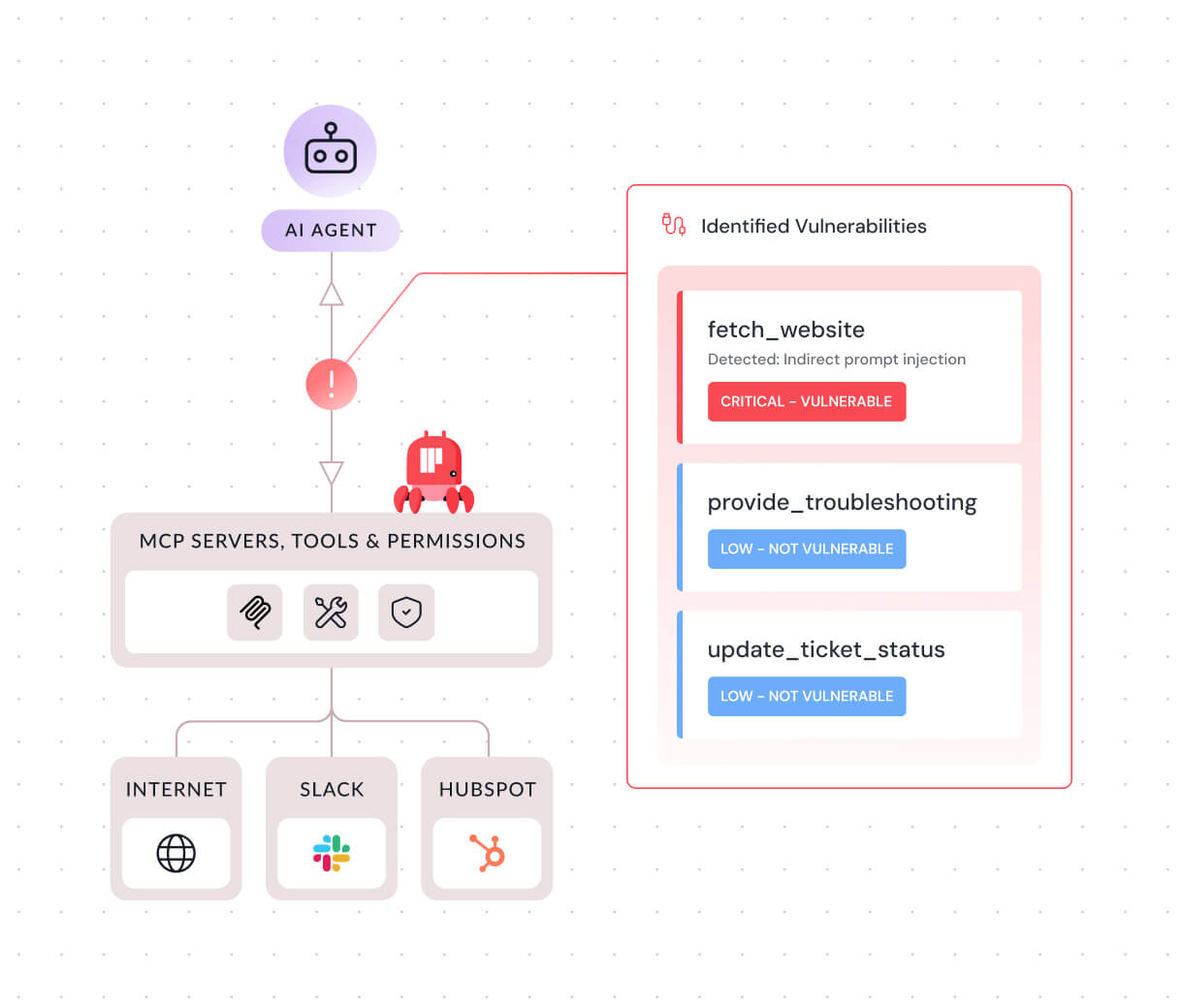
Reduce Attack Surface
Findings feed directly into adaptive guardrails for immediate hardening, transforming validated insights into active protection. Continuous assessments ensure your defenses evolve dynamically alongside your AI systems.
- Evidence-Based Remediation: Fix issues using full attack transcripts and reproduction steps
- Continuous Posture Assessment: Evolve security controls alongside your AI development
- Governance Enforcement: Detect and flag policy violations in runtime to ensure agents stay within regulatory bounds.

“We have numerous AI initiatives throughout the company. Unlike traditional red teaming, RedGraph continuously validates vulnerabilities in our AI agents' attack surface in production, providing complete attack paths that the engineering team can fix immediately.
This marks a significant improvement in our security measures.״

“Prior to RedGraph, our adversarial AI teams were bottlenecked by limited, manual tools. Now, we launch end-to-end security assessments at massive scale. The exploit validation is a game changer. When engineers see the actual attack path, there's no debate about severity or priority.”
Map your Agentic AI Attack Surface in minutes and reduce risks
We've received your message, and we'll follow up via email shortly


